- North Korean IT workers are increasingly targeting companies in Europe.
- Google Threat Intelligence Group reports that this shift follows tighter enforcement in the US.
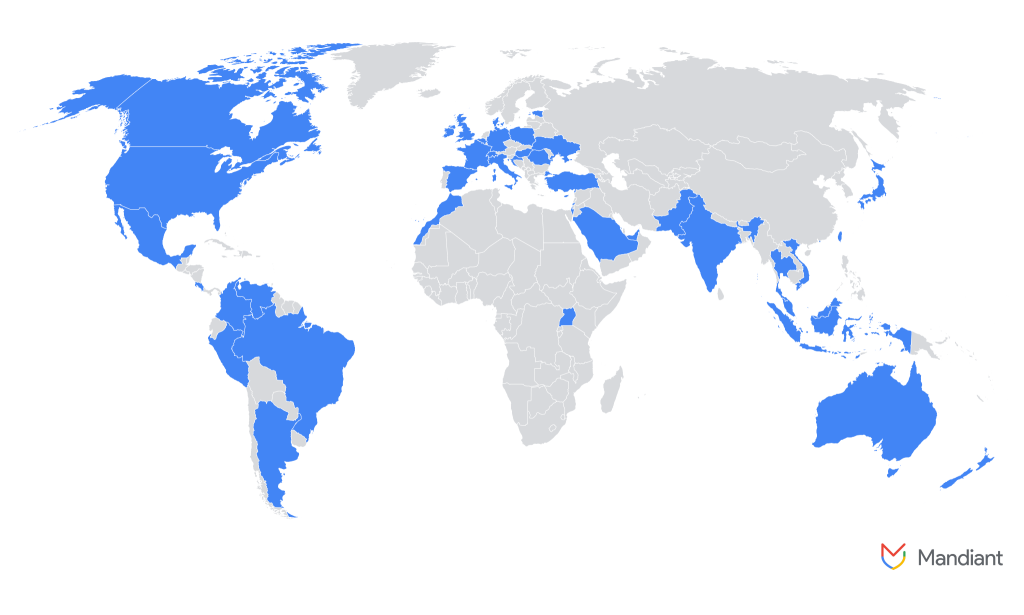
A growing number of North Korean IT workers are posing as remote freelancers from other countries in an effort to gain access to companies in Europe, raising concerns about potential espionage, data theft, and operational disruption.
According to Google’s Threat Intelligence Group (GTIG), these workers—who refer to themselves as “warriors”—are securing remote roles with foreign organisations to generate revenue for the Democratic People’s Republic of Korea (DPRK). The activity, previously concentrated in the United States, is now increasingly being observed in European countries such as Germany, the United Kingdom, and Portugal.
Since GTIG’s last report on DPRK IT worker activity, recent crackdowns in the US have made it more difficult for these individuals to secure and maintain employment there. According to a blog post by Jamie Collier, lead adviser for Europe at Google’s Threat Intelligence Group, GTIG has observed a rise in operations globally, with particular growth in Europe over the past few months. Countries targeted include Germany, the UK, and Portugal.
The workers often misrepresent their nationalities, claiming to be from countries such as Italy, Japan, Malaysia, Singapore, Ukraine, the United States, and Vietnam. They find jobs through freelance platforms like Upwork and Freelancer, as well as communication channels such as Telegram. Payments are typically made in cryptocurrency or through digital payment platforms including Wise and Payoneer.
Upwork provided a statement following publication, clarifying it did not receive the initial request for comment. The company said:
“Fraud prevention and compliance with US and international sanctions are critical priorities for Upwork. The tactics outlined in this report represent a challenge that affects the entire online work industry, and Upwork is at the forefront of combating these threats. Any attempt to use a false identity, misrepresent location, or take advantage of Upwork customers is a strict violation of our terms of use, and we take aggressive action to detect, block, and remove bad actors from our platform.
Upwork has long invested in industry-leading security and identity verification measures, deploying advanced technology alongside a dedicated team of global professionals across legal, investigations, intelligence, identity risk management, compliance, anti-money laundering, and machine learning detection. These experts work relentlessly to prevent fraudulent activity before it reaches our customers, and quickly respond to new methodologies and trends.
As fraud tactics evolve, Upwork continuously enhances its proactive screening for attempts to bypass geographic restrictions, monitoring for signs of misrepresentation both before and after contracts begin. Our sophisticated detection tools, paired with strong partnerships with law enforcement and regulatory bodies, enable us to take swift and decisive action when fraudulent behaviour is identified.
While no online platform is immune to fraud, Upwork is setting the standard for trust and safety in the industry. We will continue to invest in cutting-edge fraud prevention measures and vendor solutions, collaborate with industry stakeholders, and innovate to protect our customers and uphold the integrity of our marketplace.”
Freelancer, Telegram, Wise, and Payoneer did not respond to requests for comment.
GTIG reports that since October, there has been an uptick in cases where previously terminated workers attempt to extort their former employers by threatening to leak sensitive company information to competitors. Collier suggested that mounting pressure on these workers may be pushing them toward more aggressive tactics to maintain income.
One case in late 2024 involved a North Korean individual operating under at least 12 separate identities while applying to organisations in the defence and public sectors, reportedly using false references. In the UK, North Korean IT workers have been linked to work ranging from standard web development to more advanced projects in blockchain and artificial intelligence.
Google’s research points to risks associated with bring-your-own-device (BYOD) policies, where employees use personal devices to access internal systems. These setups often lack proper security oversight, making it more difficult to detect unauthorised access.
Authorities in the US and UK have issued multiple warnings about these activities. The FBI has advised firms to improve identity verification practices, while the US Treasury in January sanctioned two individuals and four entities accused of generating revenue for the North Korean government. Officials allege the regime withholds up to 90% of wages earned by these workers.
In a separate legal action, a US federal court in Missouri indicted 14 North Korean nationals in December for allegedly participating in an employment scheme that generated US$88 million over six years. Some of these individuals were reportedly employed by US firms for extended periods, earning hundreds of thousands of dollars without detection.
The UK’s Office of Financial Sanctions Implementation has also responded. In September, it recommended employers implement stricter identity checks, including video interviews, and advised against using cryptocurrency for payments.
Collier noted that North Korea has a long history of engaging in cyber operations to fund its regime. “A decade of diverse cyberattacks (encompassing SWIFT targeting, ransomware, cryptocurrency theft, and supply chain compromise), precedes North Korea’s latest surge,” he wrote.
“This relentless innovation demonstrates a longstanding commitment to fund the regime through cyber operations. Given DPRK IT workers’ operational success, North Korea will likely broaden its global reach. With APAC already impacted by these operations, this problem is set to escalate. These campaigns thrive on ignorance and will likely enjoy particular success in areas of APAC with less awareness of the threat.”